1 Unit
CPD technical article
There are two categories of tools that an IT auditor will need in their tool box - frameworks and technology. In this article, Mike Hughes walks us through some of the most popular industry recognised Frameworks
Reading this article and answering the related questions can count towards your verifiable CPD if you are following the unit route to CPD and the content is relevant to your learning and development needs. One hour of learning equates to one unit of CPD. We suggest you use this as a guide when allocating yourself CPD units

Introduction
Following on from my April 2024 article on building the skills of the IT auditor, I now look at the tools to assist the IT auditor, to enable them to provide an effective and professional IT audit service, the IT auditor's Tool Box.
A key objective for Internal Audit is to help and support the organisation to successfully achieve its business goals and objectives. This involves providing assurance that the organisation is operating an appropriate governance regime and the supporting management practices and controls are being effectively operated.
As organisations progress into the 21st century and conduct business and operate in the digital and cyber age, Internal Audit skills, knowledge, tools and techniques need to evolve. We can't audit 21st century systems with 20th century audit practices.
In today's business environment, all organisations, no matter how large, or small, are reliant on technology to a certain extent. Indeed, many new start-ups are totally reliant on technology to deliver their service. Uber, Airbnb, and Amazon are just a few names which spring to mind, where their whole business model is reliant on technology. Without their technology platforms, they have no business!
Therefore the IT auditor needs to keep up with the latest techniques and thinking, to allow them to effectively assess if their organisation has implemented appropriate technology/cyber governance principles and management practices for the business needs of their organisation.
This can be best achieved by the IT auditor referring to industry recognised Frameworks, which will increase the credibility to the IT auditor's assessment and conclusions on the appropriateness and effectiveness of technology and cyber related governance principles and management control practices.
Furthermore, as the technology utilised by organisations becomes more sophisticated, then the auditor needs to look to use technology to assist their audit work.
Therefore, I’m going to look at two categories of tools:
- Frameworks and
- Technology.
Frameworks
There are a number of well established and industry recognised frameworks and standards around the world, which are a very useful tool for the auditor and can be used as a reference point.
Although this is not an exhausted list, these are some of the most popular industry recognised Frameworks:
- COBIT
- IT Risk Framework
- IT Assurance Framework
- Cyber Security Essentials
- NCSC Cyber Assessment Framework (CAF)
- ENISA
- NIST Cyber Security Framework
- Australia’s Essential 8
- ISO 27001
- ISO 22301
- Managing Successful Programmes
- ITIL
Technology
There a number of different categories of automated tools, including:
- Assessment/Audit Programme
- Recommendations Tracking
- Audit Planning
- GRC
- Data Analytics
The reference to Frameworks will assist the IT auditor in their Test of Design work and the use of Technology will assist in the Testing of Operating Effectiveness.
I'm going to look at this in two parts - Part 1 will look at Frameworks and Part 2 (to be published April 2025) and will look at Technology based tools.
Frameworks
COBIT
ISACA has been a globally recognised leader in IS/IT for over 50 years. It is a professional membership organisation committed to the advancement of digital trust by empowering IS/IT professionals to grow their skills and knowledge in audit, governance, risk, cybersecurity, emerging tech and more.
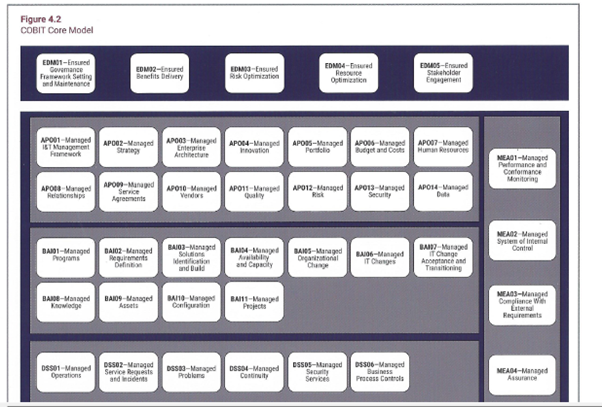
COBIT has been developed over many years by ISACA, through its network of member volunteers, who are subject matter experts. The current version of COBIT is COBIT 2019 and provides a Governance and Management Practices framework to help organisation to fully realise the positive potential from their use of technology.
COBIT Core model:
COBIT's Core Model defines Five Governance Principles, which are owned by the Senior Exec Team, setting Direction and Monitoring and Evaluating adherence to these Core Principles.
We then have the Management Practices, which implement the Governance Principles if Four Categories:
- APO - Align, Plan, Organise,
- BAI - Build, Acquire, Implement
- DSS - Deliver Service & Support
- MEA – Monitor, Evaluate and Assess.
COBIT's core philosophy is to address the following four questions:
- Are we doing the right things?
- Are we doing them in the right way?
- Are we doing them well?
- Are we delivering business value?
IT Risk Framework
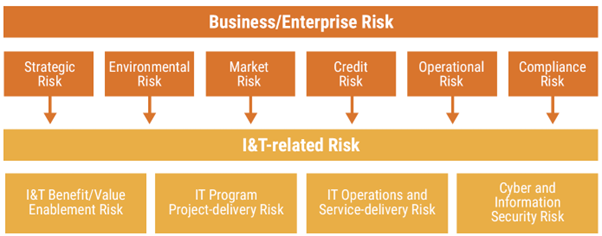
ISACA's Risk Framework helps organisations to effectively manage their business risks related to their use of technology in the cyber age, with the philosophy of the effective management of risks to help and support the achievement of the organisation’s business goals and objectives.
The framework provides a holistic, top-down/bottom-up, view of risk across the whole organisation.
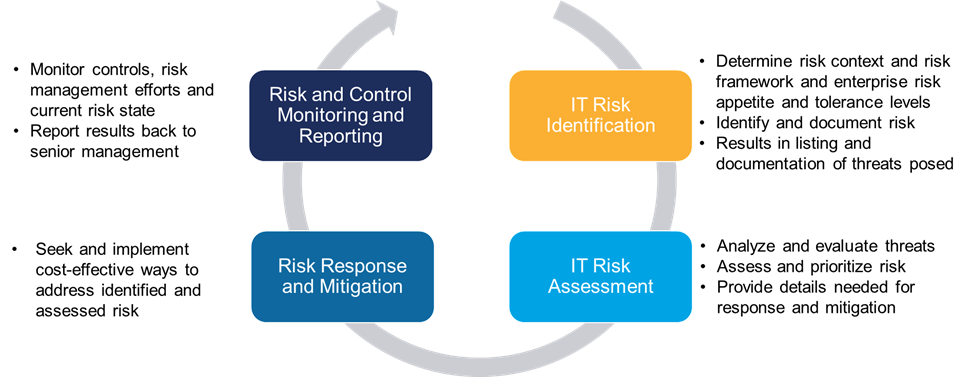
The Framework describes a continuous cyclical approach, as follows:
IT Assurance Framework
ISACA's IT Assurance Framework provides guidance and standards for conducting IT Audits and contains:
- General Standards
- Performance Standards
- Reporting Standards
ISACA's Information Technology Audit Framework (ITAF) is a comprehensive IT audit framework that:
- Establishes standards that address IT audit and assurance practitioners' roles and responsibilities, ethics, expected professional behaviour, and required knowledge and skills
- Defines terms and concepts specific to IT audit and assurance
- Provides guidance and techniques for planning, performing and reporting of IT audit and assurance engagements.
Based on ISACA material, ITAF provides a single source for IT audit and assurance practitioners to obtain guidance on the performance of audits and the development of effective audit reports.
As well as the main IT Assurance Framework, there are also a wide range of Audit/Assurance programmes, covering a number of IT Audit topics, including the following:
- Artificial Intelligence Audit Toolkit
- ISACA Cybersecurity Audit Program: Based on the NIST Cybersecurity Framework 2.0
- PCI DSS v.4.0 Audit Program
- Ransomware Readiness Audit Program
- Change Management Audit Program.
Cyber Security Essentials
Cyber Essentials is an effective, Government backed scheme that will help you to protect your organisation, whatever its size, against a whole range of the most common cyber attacks.
Cyber attacks come in many shapes and sizes, but the vast majority are very basic in nature, carried out by relatively unskilled individuals. They're the digital equivalent of a thief trying your front door to see if it's unlocked. Their advice is designed to prevent these attacks.
There are two levels of certification:
- Cyber Essentials and
- Cyber Essentials Plus.
This is a self-assessment option, which gives protection against a wide variety of the most common cyber attacks. This is important because vulnerability to basic attacks can mark your organisation out as target for more in-depth unwanted attention from cyber criminals and others.
Certification gives you peace of mind that your defences will protect against the vast majority of common cyber attacks simply because these attacks are looking for targets which do not have the Cyber Essentials technical controls in place.
Cyber Essentials shows you how to address those basics and prevent the most common attacks.
Cyber Essentials Plus still has the Cyber Essentials trademark simplicity of approach, and the protections you need to put in place are the same, but for Cyber Essentials Plus a hands-on technical verification is carried out.
Cyber Assessment Framework (CAF)
The NCSC Cyber Assessment Framework (CAF) builds on Cyber Essentials and takes it to a far more advanced level.
The CAF provides a systematic and comprehensive approach to assessing the extent to which cyber risks to essential functions are being managed by the organisation responsible. CAF-based assessments can be carried out either by the responsible organisation itself (self-assessment) or by an independent external entity, possibly a regulator / cyber oversight body or a suitably qualified organisation acting on behalf of a regulator, such as an NCSC assured commercial service provider.
The NCSC developed the CAF in its role as national technical authority for cyber security with an expectation that it would be used, amongst other things, as a tool to support effective cyber regulation. The NCSC itself has no regulatory responsibilities, and organisations subject to cyber regulation should consult with their regulators to learn whether they should use the CAF in the context of meeting regulatory requirements.
The NCSC CAF cyber security and resilience objectives and principles provide the foundations of the CAF. The 4 high-level objectives (A-D) and the 14 principles laid out within this collection are written in terms of outcomes, i.e. specification of what needs to be achieved rather than a checklist of what needs to be done. The CAF adds additional levels of detail to the top-level principles, including a collection of structured sets of Indicators of Good Practice (IGPs).
The 4 CAF high level objectives:
- Objective A - Managing security risk
- Objective B - Protecting against cyber attack
- Objective C - Detecting cyber security events
- Objective D - Minimising the impact of cyber security incidents.
ENISA
ENISA is the European Union Agency for Cybersecurity (originally the European Network and Information Security Agency). It's an EU agency dedicated to achieving a high level of cybersecurity across Europe. Established in 2004 and based in Athens, Greece, ENISA plays a key role in developing policies, standards, and practices to protect the EU's digital infrastructure and citizens from cyber threats.
ENISA provides a variety of tools and resources to enhance cybersecurity resilience across Europe. These resources cover topics such as threat intelligence, risk management, incident response, cybersecurity maturity assessments, and more. Here are some of ENISA's key tools and resources:
1. Cybersecurity Threat Landscape (CTL) Reports
- Description: Annual reports that provide an overview of the evolving cyber threat landscape in Europe. They include insights on current cyber threats, attack trends, and emerging risks.
- Use: Used by organisations and governments to understand cyber threats and enhance their cybersecurity strategies.
2. Cybersecurity Maturity Assessment Tool (CSMAT)
- Description: A tool designed to help organisations assess their cybersecurity maturity level.
- Use: Provides guidance on improving organisational cybersecurity posture, allowing stakeholders to benchmark and enhance their cybersecurity processes.
3. Incident Reporting and Management Tools
- Description: ENISA provides guidelines, templates, and tools for incident reporting in compliance with the NIS Directive.
- Use: Helps operators of essential services and digital service providers fulfill their obligations to report incidents and manage cybersecurity incidents effectively.
4. Risk Management Toolset
- Description: ENISA offers risk management frameworks, methodologies, and tools tailored for different sectors, including telecommunications, energy, finance, and healthcare.
- Use: Enables organisations to identify, assess, and mitigate risks systematically.
5. Good Practices Guides and Toolkits
- Description: Sector-specific cybersecurity best practice guides, toolkits, and guidelines for improving cybersecurity.
- Examples:
- Cloud Security Toolset: Focuses on cloud computing security best practices.
- IoT Security Standards and Guidelines: Provides IoT-specific cybersecurity frameworks and good practices.
- Use: Organisations can use these toolkits to implement effective security measures tailored to specific technology or sector needs.
6. Cyber Exercises and Training Materials
- Description: ENISA organises and supports cybersecurity exercises, including the European Cybersecurity Challenge (ECSC) and the Cyber Europe exercises.
- Use: Designed to strengthen cybersecurity response and collaboration skills among EU members and organisations.
7. Cybersecurity Certification Frameworks and Schemes
- Description: Under the EU Cybersecurity Act, ENISA develops cybersecurity certification schemes, which aim to create standards for IT products, services, and processes within the EU.
- Use: Helps organisations and vendors ensure compliance with recognised security standards, facilitating trusted and secure digital services.
8. Threat Taxonomy and Incident Classification Tools
- Description: Tools and taxonomies to classify and analyse cyber threats and incidents.
- Use: Provides common frameworks to categorise incidents and enhance threat intelligence sharing.
9. Cybersecurity Information Sharing (ISAC) Support
- Description: ENISA promotes Information Sharing and Analysis Centers (ISACs) within sectors to encourage collaboration and information exchange.
- Use: Facilitates collaboration within sectors like finance, health, and energy, allowing entities to share threat intelligence and best practices.
10. Data Protection and Privacy Tools
- Description: Resources and guidelines focused on ensuring data protection and privacy, especially relevant to GDPR compliance.
- Use: Supports organisations in meeting data protection requirements and implementing privacy-by-design.
11. 5G and Emerging Technology Security Tools
- Description: ENISA provides specific resources on securing 5G networks and emerging technologies such as Artificial Intelligence (AI) and IoT.
- Use: Helps organisations manage security in new technology domains and address challenges related to advanced connectivity.
12. Supply Chain Security Tools
- Description: Guidance on securing the supply chain in various industries, especially in the context of ICT and critical infrastructure.
- Use: Helps organisations manage risks associated with third-party suppliers and dependencies within their supply chains.
13. Awareness and Educational Resources
- Description: Educational materials, awareness campaigns, and guidance on cybersecurity awareness for both organisations and the general public.
- Use: Useful for enhancing cybersecurity awareness across all levels, from individual users to corporate employees.
NIST
NIST (the National Institute of Standards and Technology) is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness
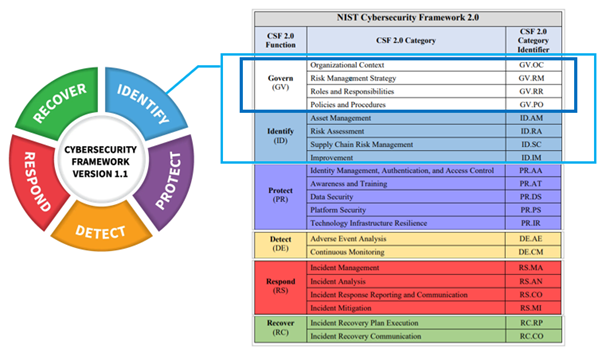
NIST provides many standards and guidance on a number of topics, the most globally adopted being NIST's Cyber Security Framework (CSF).
NIST's CSF version 1.1 is well established and version 2 was recently introduced, which added Govern to the original five NIST areas of:
- Identify
- Protect
- Detect
- Respond
- Recover
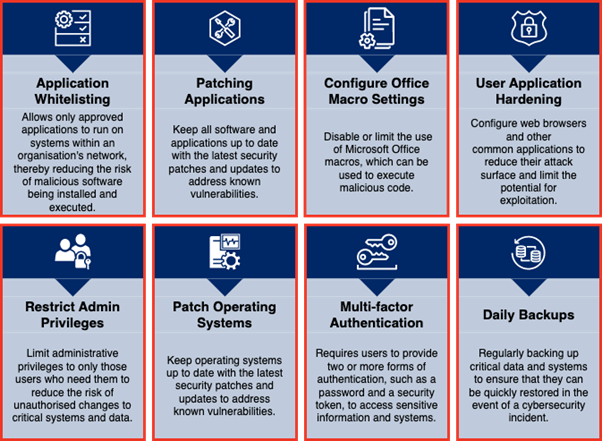
Essential 8
The Australian Signals Directorate (ASD) has developed prioritised mitigation strategies, in the form of the Strategies to Mitigate Cyber Security Incidents, to help organisations protect themselves against various cyber threats. The most effective of these mitigation strategies are the Essential Eight.
The Essential Eight has been designed to protect organisations' internet-connected information technology networks. While the principles behind the Essential Eight may be applied to enterprise mobility and operational technology networks, it was not designed for such purposes and alternative mitigation strategies may be more appropriate to defend against unique cyber threats to these environments.
The Essential Eight Maturity Model, first published in June 2017 and updated regularly, supports the implementation of the Essential Eight. It is based on ASD's experience in producing cyber threat intelligence, responding to cyber security incidents, conducting penetration testing and assisting organisations to implement the Essential Eight.
ISO 27001:2022
ISO/IEC 27001 is the world's best-known standard for information security management systems (ISMS). It defines requirements an ISMS must meet.
The ISO/IEC 27001 standard provides companies of any size and from all sectors of activity with guidance for establishing, implementing, maintaining and continually improving an information security management system.
Conformity with ISO/IEC 27001 means that an organisation or business has put in place a system to manage risks related to the security of data owned or handled by the company, and that this system respects all the best practices and principles enshrined in this International Standard.
The standard was recently revised and organisations have until October 2025 to certify to the new version of the standard ISO 27001:2022.
There are 10 main clauses, then Annex A describes 4 control categories. More detailed information can be found in ISO 27002:2022.
- Organisation Controls
- People Controls
- Physical Controls
- Technical Controls
ISO 22301:2019
ISO 22301 sets out the requirements for a Business Continuity Management System, which defines 10 clauses:
Clause 1, Scope: Sets out the organisation's scope for its Business Continuity Management System (BCMS).
Clause 2, Normative references: Sets out any normative references, external to ISO 22301 i.e. ISO 22300, Security and resilience — Vocabulary
Clause 3, Terms and definitions: Sets out the terms and definitions to be used in the organisation's BCMS.
Clause 4, Context: Your organisation must understand what it is, what it does, and what outputs and processes it must sustain. You must also determine who has a stake in the continuity of your operations — in other words, the interested parties. For example, customers have a stake in your organisation continuing to function.
Clause 5, Leadership: Few organisational initiatives thrive without the sustained support and championship of top management. Management must commit to a business continuity plan and make available any resources — human, financial, or otherwise — to ensure its success.
Clause 6, Planning: To plan for sustainability, you must understand what disruptions could potentially occur and how these incidents affect the business — in other words, potential risks and their impact. Set measurable business continuity objectives to guarantee the minimum viable products or services, as well as compliance with any legal or regulatory requirements.
Clause 7, Support: No program can advance without resources and support. Decide what personnel, roles, and teams you need for threat response and how you can best enhance their effectiveness. Create internal and external communication procedures for reference, and communicate the continuity plan to all necessary parties before and during a crisis. Establish a document management system for key continuity documents, such as procedures.
Clause 8, Operation: Conduct your risk assessment and business impact analysis, and plan your disruption recovery approach. Implement the recovery plan with detailed procedures, and test it regularly to verify that it works. Make sure people can find the procedures (and other documents) they need, and revise your plan as necessary.
Clause 9, Evaluation: Establish a process to regularly measure and assess your continuity policies and procedures and their execution. Review and revise your plan and documents to ensure they are effective and relevant
Clause 10, Improvement: Seek continual improvement in all functional and operational areas, including through periodic management reviews. Improvements in day-to-day activities help bolster the organisation in times of disruption. When processes veer from the standard or fail to conform with ISO and quality management standards, implement corrective action.
Managing Successful Programmes
Buying, building and implementing business systems continues to be a huge challenge and the main reasons why programmes/projects fail today are the same reasons of 5, 10, 15 years ago.
The Office of Governance Commerce (OGC) published Managing Successful (MSP) Programmes a number of years ago and Axelos has now taken over the up keep. MSP defines some key concepts of the System Development Life Cycle (SDLC) to help improve the chances of programme/project success.
The 5th edition of Managing Successful Programmes (MSP), was published in 2020 and introduces significant updates to align with the rapid changes in the business and digital landscape. This updated edition emphasises flexibility and agility, enabling organisations to more effectively manage complex programs, especially in environments with high volatility and frequent change. MSP 5th Edition is designed for professionals overseeing large-scale transformations, incorporating agile principles to foster adaptability, responsiveness, and structured risk management in the face of constant digital and organisational evolution.
Appendix H - Health Check is particularly helpful to the IT auditor. The Health Check appendix provides a structured tool to assess the health of a program, offering criteria and indicators that help determine whether a program is on track or if there are areas needing attention. This helps program managers and stakeholders identify any potential issues early on and take corrective action to improve the likelihood of successful program outcomes.
PRINCE2
Another Framework that has a wide adoption, particularly in UK public sector bodies is PRINCE2. PRINCE2 (PRojects IN Controlled Environments) is a structured project management methodology widely used across various industries. Developed by the UK government, it offers a clear, process-based approach that is especially useful for complex projects requiring strong governance and structure. PRINCE2 is designed to be flexible and adaptable, making it suitable for projects of all sizes.
Key Components of PRINCE2
1. Principles
PRINCE2 is based on seven principles, which provide a guiding framework for all PRINCE2 projects:
- Continued business justification: The project must have a clear reason for starting, and this justification must be maintained throughout.
- Learn from experience: Project teams should use lessons learned from past projects.
- Defined roles and responsibilities: Everyone involved should know their roles and responsibilities.
- Manage by stages: Projects are divided into manageable stages, with reviews at the end of each.
- Manage by exception: Each level of the project management structure has authority to control its own scope and can escalate issues if necessary.
- Focus on products: Projects should focus on delivering clearly defined products or outputs.
- Tailor to suit the project environment: PRINCE2 is flexible, so it can be adapted based on the project’s complexity, size, and risk.
2. Themes
PRINCE2 defines seven themes that describe critical aspects that must be addressed continuously throughout a project:
- Business Case: Ensures there's a valid reason for the project.
- Organisation: Defines and establishes project roles and responsibilities.
- Quality: Establishes the criteria for project deliverables and quality control measures.
- Plans: Outlines how plans should be structured to deliver project outcomes.
- Risk: Involves identifying, assessing, and managing project risks.
- Change: Manages any modifications in the project scope or requirements.
- Progress: Tracks project progress against the plan to ensure it stays on track.
3. Processes
PRINCE2 consists of seven processes that cover the lifecycle of the project from start to finish:
- Starting up a project (SU): Ensuring all prerequisites for initiating a project are in place.
- Directing a project (DP): Senior management's role in overall project decision-making.
- Initiating a project (IP): Laying the groundwork by defining key documents like the project plan and business case.
- Controlling a stage (CS): Managing day-to-day tasks, including monitoring progress and handling issues.
- Managing product delivery (MP): Focusing on the creation and delivery of project outputs.
- Managing a stage boundary (SB): Reviewing and planning for the next stage of the project.
- Closing a project (CP): Formally closing the project, including evaluating performance and capturing lessons learned.
4. Tailoring PRINCE2
PRINCE2 emphasises adaptability to meet the needs of different projects, encouraging project managers to tailor the methodology based on the project's complexity, resources, and stakeholder requirements.
Benefits of PRINCE2
- Clarity and Structure: The process-driven approach makes roles, responsibilities, and workflows clear.
- Scalability and Flexibility: Suitable for projects of all sizes and adaptable to various industries.
- Focus on Justification and Quality: Emphasises business case validation and quality control throughout.
- Risk and Change Management: Provides clear processes for handling project risks and scope changes.
PRINCE2 is highly regarded for its systematic approach and is often seen as a good fit for projects that require formal project governance. It is widely used in government and corporate environments, particularly in Europe, where PRINCE2 certification is often a valued qualification for project managers.
PMI PMBOK
The Project Management Body of Knowledge (PMBOK) is a comprehensive guide published by the Project Management Institute (PMI) that outlines best practices, guidelines, terminologies, and standards for project management. PMBOK serves as a foundational framework for managing projects across industries and is widely regarded as a global standard for project managers. Here is a summary of the key elements:
1. Project Management Knowledge Areas
PMBOK organises project management practices into ten Knowledge Areas that represent core competencies required for effective project management:
- Integration Management: Ensuring coordination and coherence across all project elements.
- Scope Management: Defining and managing the project's scope to ensure it meets objectives.
- Schedule Management: Planning and controlling the project schedule.
- Cost Management: Planning and managing the project budget.
- Quality Management: Ensuring the project meets defined quality standards.
- Resource Management: Efficiently managing project resources, including team members.
- Communications Management: Facilitating effective communication among stakeholders.
- Risk Management: Identifying, analysing, and responding to project risks.
- Procurement Management: Managing contracts and procurement of resources.
- Stakeholder Management: Engaging stakeholders and addressing their needs and expectations.
2. Project Management Process Groups
PMBOK organises project processes into five Process Groups, each representing a phase or aspect of a project's lifecycle:
- Initiating: Defining and authorising the project or a project phase.
- Planning: Establishing the project scope, objectives, and procedures to reach the project goals.
- Executing: Performing the work defined in the project management plan to meet the project's objectives.
- Monitoring and Controlling: Tracking, reviewing, and regulating the project's performance to ensure alignment with the plan.
- Closing: Formalising the completion of the project or phase, ensuring everything is wrapped up and documented.
3. Processes in PMBOK
PMBOK breaks down each Process Group into 49 processes that involve specific inputs, tools, techniques, and outputs (ITTOs). These processes provide a structured approach to completing tasks within each Knowledge Area, ensuring consistency and control.
4. Project Life Cycle and Phases
PMBOK emphasises that projects should follow a life cycle, typically structured around phases (like concept, development, execution, and closure). The life cycle helps ensure each phase has clear goals, deliverables, and quality measures, allowing for more manageable oversight.
5. Tailoring
PMBOK 7th Edition, released in 2021, introduced a more flexible, principles-based approach to project management, emphasising tailoring. This encourages project managers to adapt the PMBOK guidelines to fit the unique aspects of each project rather than strictly following a one-size-fits-all approach.
6. Performance Domains
The PMBOK Guide 7th Edition also introduced eight Performance Domains as areas of focus:
- Stakeholders
- Team
- Development Approach and Life Cycle
- Planning
- Project Work
- Delivery
- Measurement
- Uncertainty.
These domains are meant to improve alignment with modern project management practices and offer more flexibility and adaptability in project execution.
7. Value Delivery
The newer edition of PMBOK places a greater emphasis on value delivery, stressing that project management should be aligned with delivering business value to stakeholders and organisations. This approach acknowledges the importance of adapting to change and focusing on outcomes rather than just outputs.
8. Agile and Hybrid Project Management
The PMBOK Guide has evolved to incorporate elements of Agile and hybrid project management methodologies, recognising that traditional, predictive project management approaches may not be suitable for all types of projects. The guide now includes advice on tailoring practices to suit Agile, hybrid, or other iterative approaches.
UK Government also provides a number of tools
The UK Government provides access to a number of programme/project assurance products, tools and guidance.
ITIL
ITIL was first introduced in the 1980s in the UK to provide guidance for IT Service Delivery and Management by the UK Government's Office of Government Commerce (OGC). ITIL soon became the de facto standard, globally, for IT Service Management.
ITIL has evolved over the years and is currently overseen by Axelos. It's current version, ITIL version 4 introduced a focus on delivering business value, through operating IT Service Management practices, appropriate to deliver the quality of IT service required to meet the needs of the organisation.
There is an ISO standard, ISO 20000, but in practice we see far more organisations adopting ITIL.
ITIL v4 builds upon ITIL 3's five core areas:
ITIL v4 is built on 7 Guiding Principles:
- Focus on Value: Deliver value at every stage.
- Start Where You Are: Assess the current state before moving forward.
- Progress Iteratively with Feedback: Implement small, incremental improvements.
- Collaborate and Promote Visibility: Engage stakeholders and keep processes transparent.
- Think and Work Holistically: Ensure all parts work together seamlessly.
- Keep It Simple and Practical: Avoid complex solutions when simpler options exist.
- Optimise and Automate: Use technology to streamline tasks wherever possible.
The main change in ITIL v4 brought the focus of delivering business value, therefore ITIL v4 defines a Service Value System (SVS) which integrates various components to create value:
- Opportunity & Demand: Recognising the needs and opportunities that the service should address.
- Guiding Principles: Direct decision-making at every level.
- Governance: Sets policies and ensures accountability.
- Service Value Chain (SVC): The core operational model.
- Practices: The ITIL processes needed to accomplish work.
- Continuous Improvement: Ongoing improvement of products and services.
ITIL v4 also defines a Service Value Chain (SVC), which describes the key activities required to create value:
- Plan: Define goals, policies, and guidelines.
- Improve: Enhance service performance continuously.
- Engage: Interact with stakeholders to understand their needs.
- Design and Transition: Develop new services and manage change.
- Obtain/Build: Source or build components of services.
- Deliver and Support: Ensure service delivery meets quality standards.
Wrap-up
Internal Audit has a crucial role in helping organisations to effectively manage their business risk of using technology and to help to support the delivery of the business goals and objectives as organisations of all sizes become increasingly reliant on technology operating in the digital and cyber world.
Therefore, Internal Audit has a crucial role to play and as auditors, we need to be constantly developing our knowledge, skills and learning to adapt to the changing risk environments of our organisation and helping to effectively mange risk. A pragmatic and efficient means to achieve this is through the reference to industry recognised Frameworks.
I end this piece with a Health Warning. The definition of a Framework is: “a system of rules, ideas, or beliefs that is used to plan or decide something”.
So, a Framework is what it “says on the tin”. It is a framework defining a number of principles, and the organisation needs to determine which are appropriate for their needs and to aid consistent implementation across the whole organisation. They are not prescriptive, which demands that every principle is implemented exactly to the letter of the Framework.
Whilst the IT auditor can reference Frameworks, the auditor still needs to use their skills, experience and judgement to use and adapt these Frameworks, so they are appropriate for business needs of their organisation.
Mike Hughes, ChCSP, CISA, CISM, CGEIT, CRISC, CDPSE, MIoD - Mike is Past President and the current Director of relationships of ISACA Central UK and has been involved with ISACA for over 32 years, at both the Local and International levels. Mike has served on a number of ISACA’s Internal Boards and Committees, including a term on ISACA’s Internal Borad of Directors and he is currently a member of ISACA’s UK Advocacy Task Force. As well as holding a number of ISACA’s certifications, including CISA, CISM, and CRISC, Mike is also one of ISACA’s trainers for the exam preparation courses for these certifications. Mike is also a Chartered Cyber Security Professional of the UK Cyber Security Council. Mike’s many years of volunteering with ISACA was recognised in 2023, when he was inducted into ISACA’s prestigious, Hall of Fame. Mike has over 40 years experience, including 10 years in mainstream IT, 20 years with KPMG in a number of senior roles and for the past 16 years as a Director with Prism RA, a technology and cyber governance, risk, compliance and security consultancy. Mike has extensive IT Audit experience, including having been KPMG’s UK IT Audit Service Line Lead and KPMG Midlands Governance & Compliance lead. Mike continues supporting a number of Internal Audit Teams to help deliver their IT Audit capability. Mike is also a non-executive director of Cyber Q Group, an award winning, innovative cyber security company.
1 Unit